[ad_1]
The malicious code is stored in * .doc files, which are attached to the email. lyrics. The attached file contains the executable code for PowerShell. When you open the attached file, the PowerShell executable code is launched and an executable * .exe file is sent to the user’s computer. The malicious code tries to collect personal information from the user of your computer, such as email. email information (login details, contact information, emails).
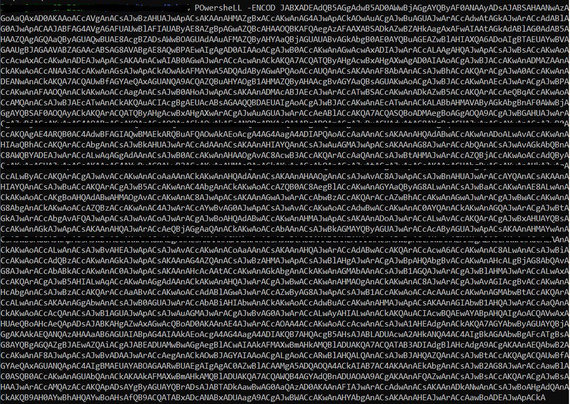
Powershell code

Powershell code partially decoded
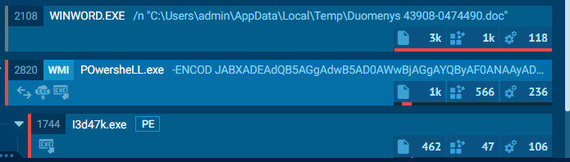
Operation algorithm
 The. Text of the letter (if applicable) is usually written in Lithuanian. The letter appears real to the recipient as it is sent by a known and trusted recipient, but is in fact forged.
The. Text of the letter (if applicable) is usually written in Lithuanian. The letter appears real to the recipient as it is sent by a known and trusted recipient, but is in fact forged.
recommendations
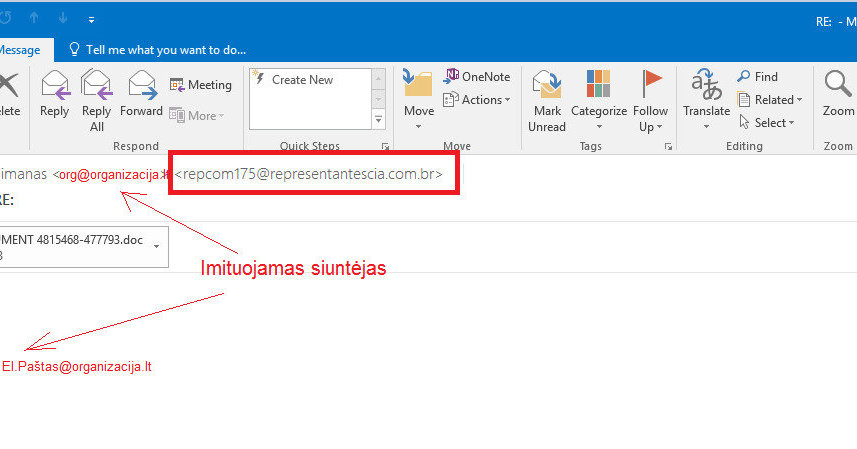
Check the message headers to see who the actual sender of the email is (box Since). When analyzing the headline, you must first look at Received parameter from the bottom. This setting will tell you which server the email was sent from. lyrics. Yes Since the field is [email protected], am Received the address field (domain) “imone.lt” must be visible in the field. In the case of this fraud in the box Received completely different data from which the letter was sent is visible. See fig. Four.
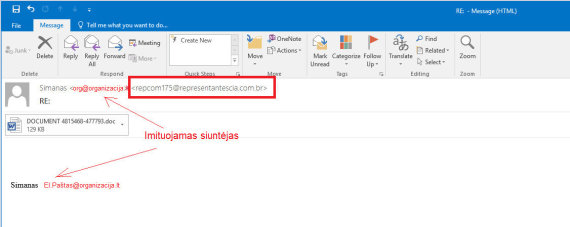
Fake email the actual sender of the letter
According to the email. mail programs, the ability to view headers varies. Be aware that cybercriminals regularly distribute other malicious code that exploits vulnerabilities in various software programs, so we recommend that you keep your antivirus, operating system and other software up to date. To protect yourself from email We recommend that you enable and properly configure the Sender Policy Framework (SPF) functionality. This tool should be used with special care, as incorrect settings can lead to some emails not being delivered to their recipients.
We remind you that the main thing is to be constantly attentive and critical of incoming letters.
Recommendations for open emails email with malicious code
1. Send an email to all computers where the email was opened. emails with malicious code, verification. Scan computers with up-to-date security measures or online scanners from reputable antivirus manufacturers.
2. Install the latest patches for the operating system and the programs used.
3. Change the passwords for the accounts used on your computer (email, social media, etc.).
[ad_2]