![]()
[ad_1]
By releasing contact blocks to resuscitate the economy, many await the intelligent help of tracking applications. However, the technical implementation is error prone and presents the risk of misuse.
SARS-CoV-2 has become a global pandemic because the virus is faster than health systems. When a patient feels the first symptoms and signs up for the test, the Robert Koch Institute says an average of five to six days have passed since infection. However, three days before the onset of the disease, an infected person can transmit the virus to others. Only when the test result is available after two days, employees clarify in extensive interviews who may have been infected. Until these contacts are identified and warned, a newly infected person has often inadvertently spread the virus.
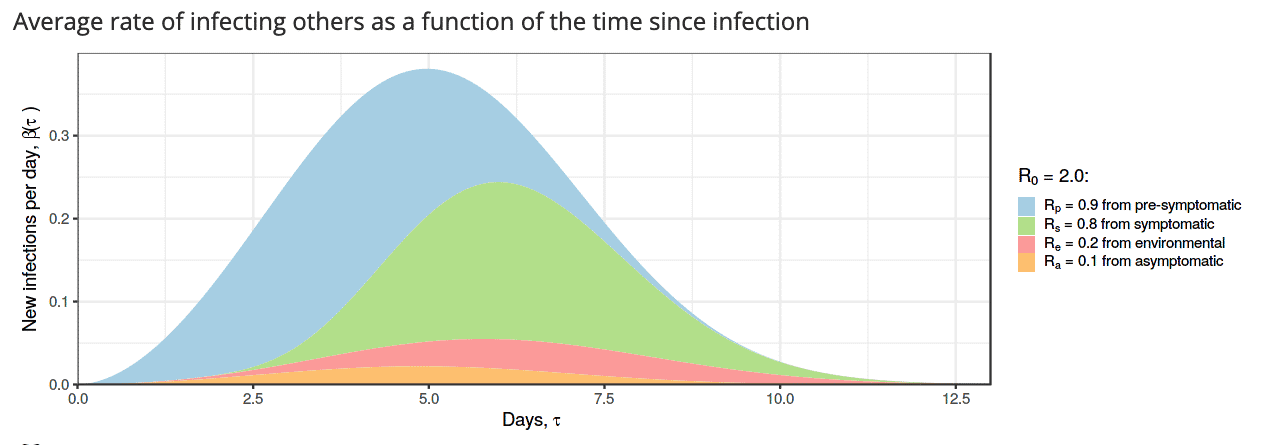
Tracking apps aim to warn newly infected people before they experience symptoms and thus weaken the blue part of the infection curve (here, for example, with a doubling time of 5 days).
(Image: Michelle Kendall)
This is also confirmed by an Oxford study published by Luca Ferretti with colleagues in late March. Consequently, the highest risk of infection comes from infected people who still do not show any symptoms of Covid-19 (shown in light blue on the graph). They make up half of all transmissions. The second most common infection is from patients with symptoms (green curve). In contrast, indirect environmental infections (red curve) and those infected without symptoms (orange curve) play a minor role.
According to Ferretti, the only way to stop exponential spread is to contain light blue group infections. This is exactly where tracking apps come in, which should dramatically reduce notification time, so newly infected people can isolate themselves before showing symptoms. The light blue portion of the infection curve would flatten out. To control the epidemic, a total of approximately two out of three infections would have to be prevented.
Approaches are based on Bluetooth
Because direct contact with infected people is primarily responsible for the spread of SARS-CoV-2, but indirect smear infections across surfaces play little role, the location of those affected is not relevant. An app just needs to register focus for other people. GPS tracking, as practiced by some countries in Asia and Israel, is neither necessary nor practicable in cities with high-rise buildings.
That is why around a dozen global approaches rely on Bluetooth. Smartphone apps are supposed to recognize which people an infected person has been approaching for how long, so the virus could have been transmitted. To do this, both of them must use their smartphones or a smart watch on their bodies. The applications installed there transmit to each other a temporarily valid identification and the device type of the smartphone, which are stored in encrypted form on the smartphone along with the measured Bluetooth signal level, time and duration of the encounter. If a user tests positive for Covid-19, they obtain a TAN with which the application transmits their IDs to a server that informs the contacts. Otherwise, the app will remove outdated contact information after a specified period of two to three weeks. All Bluetooth 4.0 smartphones, which Apple first used nine years ago on the iPhone 4S, support swapping.
Therefore, manufacturers have to solve two technical problems when implementing the applications: first, they must measure the distance of the devices as accurately as possible through Bluetooth, so that only those contacts that were actually in the radio are saved infectious around two meters long enough. Second, they must secure the storage and sharing of identifications so well that they are only used to warn of an infection in an emergency and are not misused by third parties to monitor or trigger false alarms.
Difficult measurements
Singapore is one of the first countries to use such a Bluetooth application for contact monitoring. The TraceTogether application was launched on March 20 for Android and iOS. In mid-April, Singapore released the underlying BlueTrace system code on GitHub, which includes information on calibrating Bluetooth transmitters and receivers on smartphones.
To determine the distance via Bluetooth, the receiver must measure the signal level of the transmitter. Unlike permanently installed beacons in museums and shopping malls, smartphones do not transmit with calibrated performance. Developers in Singapore found differences of 30 decibels (factor 1000) in different models. Even with one and the same smartphone, the level fluctuated so significantly that it was only possible to estimate distance by weighting many measurements over a longer period of time. TraceTogether only saves contacts that last at least half an hour. Other concepts require a contact time of 15 minutes.
The levels of the Bluetooth signals fluctuate considerably even with a constant distance between different smartphones and make it difficult to measure the distance.
(Image: BlueTrace)
Also, developers were struggling with iOS power saving modes. They prevent apps from regularly scanning Bluetooth devices in the background and sending their own ID. Therefore, on an iPhone, the tracking app should always be in the foreground, which is not very practical if you want to do a little surfing on a busy train or in the waiting room. Android also supports tracking in the background.
Apple and Google are required to solve the fundamental problems with fluctuating transmit power and power saving modes. At Easter, the two companies announced that they would offer joint solutions for monitoring contacts via Bluetooth. Apple plans to release an update for iOS in mid-May. Since Android makes it much more difficult to play corresponding system updates for all smartphone manufacturers, Google relies on its own tracking app on the Play Store.
Central IDs
In their previously rudimentary concept, Apple and Google largely follow the European approach to PEPP-PT. The Swiss-based non-profit organization Pan-European Privacy-Preserve Proximity Tracing now has 130 members from across Europe, including various Fraunhofer universities and institutes. The DP-3T open protocol is the most advanced. Its developers have published a detailed analysis on GitHub, which examines possible attack scenarios for a tracking application.
The central point is the output of identification IDs under which contacts are saved and notified in the event of an infection. IDs change every few minutes to make it difficult to track people. Additional timestamps make replay attacks more difficult, in which an attacker records a Bluetooth signal and then plays it elsewhere. You could use it to counterfeit missed contacts and specifically send people to quarantine, even though they are not at risk.
In Singapore, the Ministry of Health creates temporary IDs on a central server, distributes them to applications from there, and stores the associated phone numbers. If an infected person is positive, their application sends the encrypted contact IDs on their smartphone to the central server. This verifies the integrity of the IDs, determines the duration and proximity of the contacts, and sends warnings to those affected.
With this central focus, the Singapore Ministry of Health discovers who a positive test person has had contact with in the past three weeks and could use this information to create detailed profiles.
Decentralized solution
The PEPP-PT approach, which is also followed by Google and Apple, favors a decentralized solution. Smartphones generate temporary IDs and exchange them with each other. If an infected person is positive, he must send his contacts to a server himself. Simply put, the server sends all incoming IDs of potential infected people to all smartphones every day. They compare them to their own history IDs and warn the user if they match. In this way, contact persons can be notified without the identity of the server or the infected person.
However, according to the DP-3T manufacturers, this decentralized system is also vulnerable, albeit with greater effort. If someone distributes multiple Bluetooth receivers in a city, they could possibly create movement profiles of infected people. To make this difficult, DP-3T developers propose various measures where IDs are broken into chunks and encoded so that only owners’ smartphones can calculate if they are affected. However, this would increase the volume of daily data transfers.
If such tracking applications are secure when they come on the market, they would have to be verified externally and independently. TÜV Informationstechnik GmbH, for example, offers such tests for crown applications free of charge, Managing Director Dirk Kretschmar told c’t. Security against hacker attacks, compliance with the GDPR and other data protection regulations will be verified. An initial evaluation at level 1 would take at least five business days, a complete review at level 3 up to two months. In order to use such an application as soon as possible, you may have to compromise at first, and the benefits of containing the pandemic against data protection issues may outweigh.
(witch)
More information about app tracking against Corona:
PEPP-PT documentation of the monitoring system of April 18
This PEPP-PT documentation was released shortly after the editorial deadline of April 16.
ROBERT – Robust Proximity Tracking and Privacy Preservation (FRAUNHOFER AISEC, Germany)
ROBERT – GitHub repository
DP-3T White Paper with Attack Scenario Analysis
A day after the editorial deadline of April 16, DP-3T announced that they had abandoned PEPP-PT. The reason given by Professor James Larus of DP-3T was the fundamental dissent over a technical solution that PEPP-PT propagated. What is meant is the proposal for the decentralized generation of IDs, as proposed by DP-3T in this document.
Fraser Group (Oxford, UK)
TCN Coalition (international)
BlueTrace White Paper
Hamagen (Israel)
Covid Watch (USA)
PACT Protocol (United States, West Coast)
PACT Protocol (United States, East Coast)
Safe routes from MIT (USA)
This article comes from c’t 10/2020.