
[ad_1]
Unknown criminals simultaneously hijacked a fairly large number of known people’s and companies’ Twitter accounts, announcing that they were overwhelmed by generosity, and that anyone transferring cryptocurrencies to the specified bitcoin wallet address will receive double the same amount. of cryptocurrencies. It goes without saying that it is not the pot of gold that awaits those you trust, but the tears in the broken garden. Cybercriminals are already enjoying the pot of gold: Approximately one hour after the spread of fraudulent messages, at least 11 bitcoins have been added to their account (at the current rate, more than 88,000 euros).
Programmers were able to simultaneously take over billionaire, businessman, CEO of Tesla and SpaceX, Elon Musko, one of the richest people on the planet Bill Gates, another wealthy man who also led the world in his wealth Jeff Bezos, candidate for the 5 presidents Americans Joe Biden, transportation business leaders Uber, Apple and many other accounts.
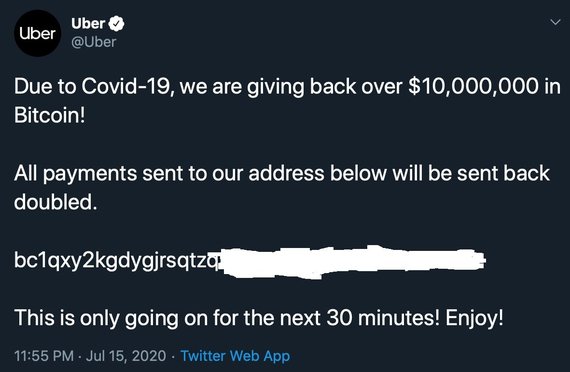
Twitter photo / Uber Twitter account hacked
TechCrunch announces that taking control of accounts will immediately change your login password and the email address that account is registered with, making it difficult to return to the payee.
According to CNN, this cyber attack is probably the biggest cyber security incident in Twitter’s history, due to the number of accounts taken by known people and companies. And it’s not just a matter of concern that trustworthy people may suffer financially, a social network used by a host of heads of state, some of whom, including United States President Donald Trump, want to post important political decisions on Twitter. . Assuming the account of such a head of state could lead to difficult reparations and a global crisis.
A Twitter user called this coordinated attack, which could have not only serious financial consequences, but also a significant worldwide impact of cyber security, a “tweeter.”
Twitter’s cybersecurity team is aware of this attack, but has not yet announced the path of the attack, but there is no shortage of different versions in the public domain: individual leaked passwords have long accumulated and are used to hack account from a Twitter employee. Thus gaining greater privileges, taking advantage of a 0-day vulnerability to access Twitter servers, hacking the Twitter message distribution tool (API).
[ad_2]