[ad_1]
Security experts from Austria, Germany and Great Britain have discovered a new gateway for attacks on processors, especially from Intel: the “Running Average Power Limit” (RAPL) function, with which you can read and influence the consumption of power of a CPU during operation. With RAPL, secret keys for cryptographic algorithms like AES can also be unmasked with some effort, even if they are in a supposedly secure Trusted Execution Environment (TEE), which was configured by Intel Software Protection Extensions (SGX). The security hole was given the name Platypus (platypus), which means “Power Leak Attacks: Targeting Your Protected User Secrets.”
RAPL interface
The RAPL interface is designed to monitor and control server processors, especially in data centers (in the cloud). Linux provides a “Power Limiting Framework” for this. If, for example, part of the cooling system or the power supply fails, the maximum power consumption of the servers can be limited to prevent overheating or downtime. However, RAPL also reveals, among other things, how much power the CPU is currently consuming.
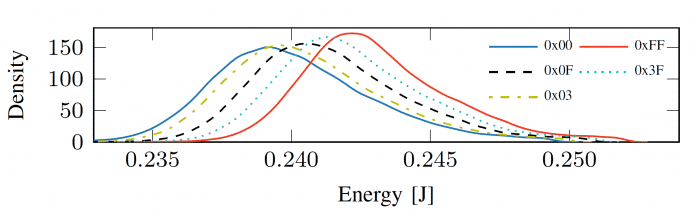
Distribution of the energy requirement when processing the imul command with two operands, one with the value 8 and the other with Hamming weight change (from 0x00 to 0xFF).
(Image: TU Graz / CISPA / Uni Birmingham)
The power consumption of an arithmetic unit changes depending on the type of calculation you are currently performing. Side channel attacks that take advantage of this connection to draw conclusions about processed data have been known for decades. That is why security chips have special functions for money cards, smart cards and pay TV cards that protect against such attacks.
Energy leak attack
Most “power leak” attacks require the attacker to have physical access to the target system in order to connect a power meter or oscilloscope, for example. Platypus’s attack now also works remotely; the RAPL digital interface can even be queried from the operating system without administrator rights.
However, until now, experts have opined that RAPL data is not accurate enough to be able to recognize a single RSA key, for example. According to the discoverers of Platypus, RAPL allows about 20,000 measurements per second, which is very little compared to the nearly 5 billion clock cycles that each of the 28 cores of an Intel processor go through per second. But if the RAPL measurement can last long enough, the secret values can be determined bit by bit by statistical analysis of the power measurements (Differential Power Analysis / DPA and Correlation Power Analysis / CPA).
Platypus Attack – Reading AES keys from an Intel SGX enclave through the RAPL interface of the Intel CPU.
Security researchers Moritz Lipp, Andreas Kogler, Catherine Easdon, Claudio Canella, and Daniel Gruss from TU Graz, David Oswald from the University of Birmingham, and Michael Schwarz from CISPA used numerous tricks to refine the measured RAPL values sufficiently to access data and instructions to close. For example, they developed methods to be able to superimpose repeated measurements with sufficient precision.
They also eliminated inaccuracies, because Intel’s RAPL interface only provides data for all CPU cores together and not for each individual. They also included information on the respective core voltage.
Attacks on KASLR, TLS and SGX
To make malware attacks more difficult, the Linux kernel scrambles RAM addresses; this is called Kernel Address Space Layout Randomization (KASLR). A Platypus attack should be able to distinguish between valid and invalid memory addresses within 20 seconds.
Unmasking an RSA key in the mbed TLS encryption library took much longer, 100 minutes. And to get a key processed with AES-NI commands from an SGX enclave, the attack had to run for at least 26 hours. However, if many I / Os interfered with the RAPL signal, the attack lasted more than 270 hours, that is, more than 10 days.
Platypus attack on Linux kernel address space layout randomization (KASLR).
This already suggests that Platypus will probably not be used for generalized attacks; it is particularly important for cloud servers and less so for desktops and laptops.
Intel is already making patches available in the form of microcode updates, which reach affected systems in the usual way, either through BIOS or operating system updates. These are all with Intel Core i and Xeon series processors from the Sandy Bridge generation introduced in 2011, that is, Core i-2000, Pentium G, Celeron G, Xeon E5-2000 and E3-1200.
According to the researchers, other processors are also affected, for example, they were able to perform similar measurements on various AMD Ryzen systems, but administrator rights were required to access RAPL there.
Microcode Updates Announced
Intel explains the Platypus attack in Intel Security Advisory Intel-SA-00389. As a remedy against Platypus attacks, microcode updates ensure that measurements are less accurate when a CPU core processes SGX commands. Linux kernel updates also prevent unprivileged users from accessing certain RAPL data. The CVE numbers are CVE-2020-8694 and CVE-2020-8695.
Platypus co-discoverers Moritz Lipp, Daniel Gruss, and Michael Schwarz were already involved in uncovering the CPU, Specter, and Meltdown vulnerabilities. Daniel Gruss also worked on the Plundervolt security hole investigation, which manipulates the internal registers of the CPU as a side channel to control the power supply.

(tail)
