[ad_1]

Kaspersky Lab security researchers found threat actors who exploited the Google Play Store for years to distribute advanced Android malware to steal a wide range of sensitive user data. According to the researchers, a malicious campaign called “PhantomLance” has targeted Android devices with malware and spyware payloads built into apps delivered across multiple platforms, including Google’s Play Store and other Android app stores like APKpure and APKCombo. .
“The campaign has been active since at least 2015 and is still ongoing, featuring multiple versions of complex spyware (software created to collect victim data) and smart distribution tactics, including distribution via dozens of apps on the official Google Play market. ” Kaspersky said.
Evasion of Google’s security controls
The researchers found that the attackers behind the campaign used sophisticated techniques to constantly bypass the investigative process that Google uses to detect malicious applications. Hackers initially submit a benign version of an app and include the back door once Google accepts it.
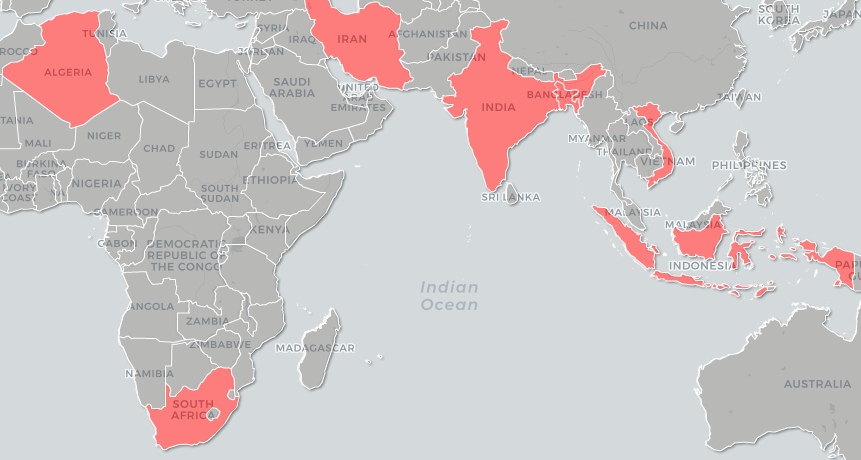
Kaspersky observed more than 300 infection attacks on Android device users in India, Vietnam, Bangladesh and Indonesia since 2016. Several threat detections were also detected in Nepal, Myanmar and Malaysia. Below is a cartographic representation of countries with the main attack attempts.
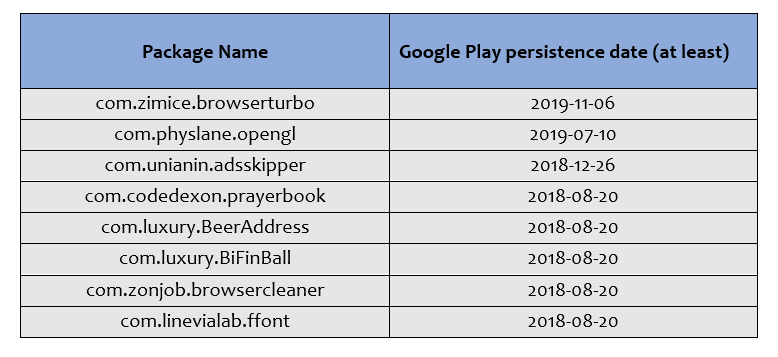
In addition to Android apps that contain PhantomLance malware, Kaspersky also provided a list of apps that Google distributed and then removed from the Play Store in November 2019.
“During our extensive investigation, we discovered a certain tactic often used by threat actors to distribute their malware. The initial versions of the applications loaded in the application markets did not contain any malicious payload or code to drop a payload. These versions were accepted because they contained nothing suspicious, but the tracking versions were updated with both malicious payloads and code to remove and run these payloads. We were able to confirm this behavior in all samples, and we were able to find two versions of the applications, with and without a payload, ”added Kaspersky.
[ad_2]