[ad_1]

A highly compelling phishing campaign is to use cloned images of automated Microsoft Teams notifications in attacks that attempt to obtain Office 365 credentials.
The Microsoft Teams cloud collaboration platform has seen a large increase in usage since the start of the COVID-19 pandemic, and Microsoft announced on March 30 that the platform has reached 75 million daily active users (DAUs), with a 70% increase since March 19 when it reported 44 million DAU.
Phishing emails that spoof Microsoft Teams file sharing and audio chat notifications have so far reached the inboxes of 15,000 to 50,000 targets based on statistics from researchers like the security company. Abnormal Security email address.
What makes them even more dangerous than regular phishing messages is that users are used to receiving alerts from various online collaboration services to keep in touch with colleagues, friends and family, and makes them prone to ignore any signals that Otherwise it would allow them to realize that they are being attacked.
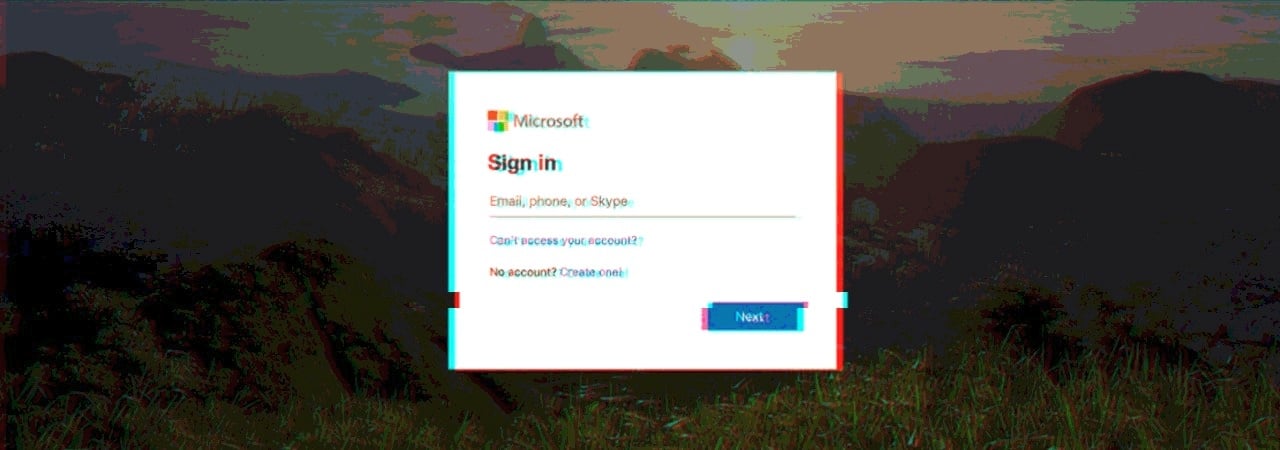
Cloning login pages to steal Office 365 accounts
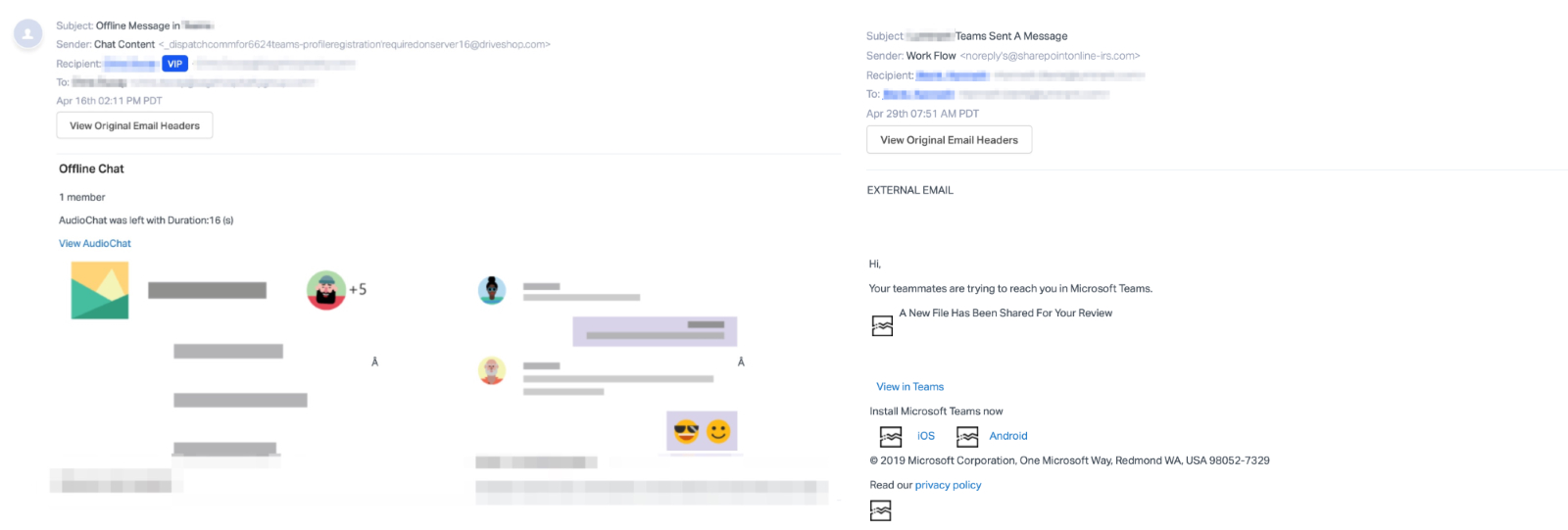
What makes these phishing attacks special is cloning Microsoft Teams alerts instead of creating them from scratch using mismatched images collected from all over the place and content riddled with typos and grammatical errors.
“Since the images found during this attack are actual images used by the legitimate provider, the recipient may be more convinced that this is a legitimate email,” the researchers said. “This is especially true on mobile devices where images take up most of the content on the screen.”
Some of the phishing emails the researchers were able to collect alert potential victims of offline audio messages and invite them to listen to them, while others will let them know that their teammates are trying to communicate with them using Microsoft Teams. .
The latter will also inform the targets of the shared files for review and will also provide them with links to install the Teams client on iOS and Android devices.
As things stand, this campaign should be able to bypass some secure email gateways (SEGs) and convince many more targets to visit the phishing homepage instead of sending the email to the spam.
To evade email protection services, attackers also use various URL redirects with the ultimate goal of hiding the URL used to host the phishing campaign.
In one of the attacks, for example, “URL redirection is hosted on YouTube, then redirected twice to the final web page that hosts another Microsoft login phishing credential site.”
In another version of these attacks, the phishing email is sent from a recently registered domain, sharepointonline-irs[.]com, which is not associated with Microsoft or the US Internal Revenue Service (IRS). Although he tries to convince the objectives to the contrary.
Landing pages also use the same graphics that are shown in the Microsoft Teams web notifications that they mimic, with the final effect of showing the target a perfectly cloned version of the actual product.

After jumping through all the hoops, the targets will land on a fake and, again, perfectly cloned into the Office 365 login form that attackers use to obtain victims’ credentials.
“If the recipient is a victim of this attack, this user’s credentials would be compromised,” the researchers explain.
“Also, since Microsoft Teams is tied to Microsoft Office 365, the attacker can access other information available with the user’s Microsoft credentials through single sign-on.”
Microsoft computers, phishing and credential theft
The Microsoft Teams client was recently patched to correct a security vulnerability that allowed attackers to take over users’ accounts by sending them an animated GIF image.
Microsoft’s Sway service is also posing as a phishing campaign called PerSwaysion to trick potential victims into sending their Office 365 login credentials to multiple threat actors.
To date, the operators behind these attacks have managed to collect more than 20 Office 365 accounts belonging to executive companies in the US. Canada, Germany, the United Kingdom, the Netherlands, Hong Kong and Singapore.
Phishing campaigns are also targeting users of Zoom, another cloud collaboration platform that has seen explosive growth this year, with fake Zoom meeting notifications being used to steal email addresses and passwords from the victims.