
Updated: September 17, 2020 6:54:16 am
 The Indian Express attempts to frame the context given the prevailing situation on the India-China border, the scale and legality of the operations, the technology involved and the possibilities of end use, given the wealth of information that is being collected.
The Indian Express attempts to frame the context given the prevailing situation on the India-China border, the scale and legality of the operations, the technology involved and the possibilities of end use, given the wealth of information that is being collected.
The Government of India decided on Wednesday to establish an “expert committee” under the National Cyber Security Coordinator in the Secretariat of the National Security Council following a three-part investigation series of The Indian Express. The committee will study the reports, assess their implications, assess any violations of the law, and present its recommendations within 30 days.
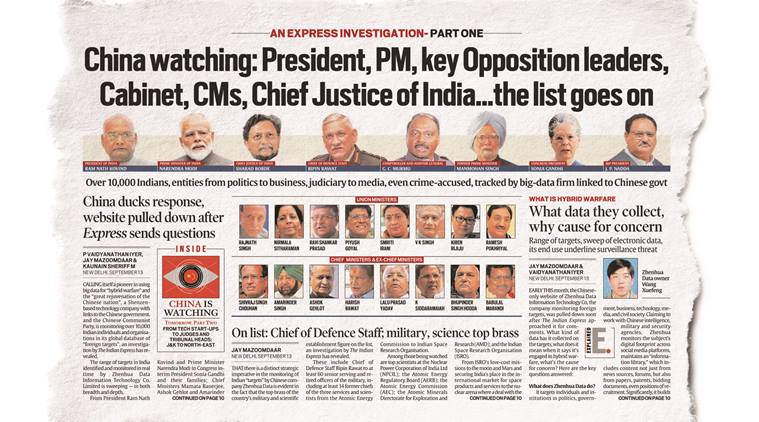
The series reveals how a Shenzhen-based information technology company, Zhenhua Data, with ties to the Chinese government and military, is monitoring more than 2.5 million people around the world, including at least 10,000 Indians. The investigation has elicited various responses.
The Indian Express attempts to frame the context given the prevailing situation on the India-China border, the scale and legality of the operations, the technology involved and the possibilities of end use, given the wealth of information that is being collected.
The bottom
Over the past decade, the rapid evolution of Internet technology, cheap phones, and cheaper data have transformed the lives of urban and rural Indians in ways that now seem irreversible.
With smartphones becoming more ubiquitous, technology improving accessibility, and probably the cheapest data in the world (6.5 rupees per GB), nearly all phones are data devices today.
The heavy emphasis on the digitization of government services by Prime Minister Narendra Modi, and the demonetization of Rs 500 and Rs 1000 bills in November 2016, have turned mobile phones into almost a KYC device that is linked to the individual and your identity: Aadhaar authentication is provided by mobile phone; Instant transfer of funds between bank accounts is enabled through UPI.
Now, three out of every four smartphones sold in India during April-June this year were Chinese brands; in the previous quarter, four out of every five phones sold were Chinese. Most phones also come pre-installed with Facebook, Google, YouTube, and many other social media platforms.
Explained | Could the war with India be an attempt to restore Xi’s unstable political position in China?
India has banned 224 Chinese apps, including TikTok, CamScanner, and PUBG. In the US, TikTok will soon change hands. What is at the center of such actions in India and the West is the fear at the application level, and also at the pipeline level (with companies like Huawei and ZTE), that personal data could be compromised and could reach the servers. Chinese. . Beijing denies it, but countries are skeptical and become more cautious, given the nature of an assertive and ambitious China, which today is seen as expansionary.
Question of legality
Zhenhua Data has obtained personal information from a dozen social media platforms and many other online sources. At the heart of the legal argument is the basic assumption: can the consent given to Facebook, Twitter, Wiki, Medium, Youtube and Instagram, etc. be taken. as consent for a third party to extract information from these platforms?
Two decades ago, this could have been fine. But the exponential increase in processing power, the rapid evolution in big data analytics and artificial intelligence, has completely changed the paradigm.
It is increasingly evident that companies have nothing to do with what is said, written or appears on their platforms; they do not claim intermittent liability.
The Personal Data Protection Bill, once it becomes law, will place responsibilities on the platforms, be it Twitter or Facebook, which are the main data collectors, to keep personal information safe.
There will be intermediaries such as account aggregators and consent managers, who will keep a tab on these platforms and their possible misuse.
But can these platforms or the intermediaries really act against a sovereign nation like China, if it is the main source of misuse?
Operations and scale
Zhenhua Data has collected information on approximately 2.5 million key people and more than 650,000 organizations from countries around the world.
There are thousands of people in India, along with their network of families and associates tracked on multiple social media platforms. India’s database includes prominent people: ministers, businessmen, businessmen, defense personnel, bureaucrats and diplomats, academics and researchers, scientists and academics.
The first question that arises is:
What’s the use of tracking down public figures, about whom so much is known anyway?
That’s exactly the motivation, because tracking them gives you insight into the minds of their followers. The way followers or friends react (like / share / comment) to any public figure on open platforms reveals a lot about each of them.
Zhenhua Data is not necessarily interested in all followers of a public figure. But that’s the thing about big data. It is about casting the network as wide as possible where individuals are not necessarily a target as consequential in themselves, but simply because they complete the wide arc. The more information that is collected and correlated, the more that can be discovered. Leaving out certain members of, say, a leadership team of any configuration because they are not exciting enough defeats that purpose.
The second question that follows is:
So what, many companies have been doing this for years, both in India and other countries?
Like any big data operation involving OSINT (open source intelligence), Zhenhua Data deals with volumes.
First, the sweep: how many people it tracks. Second, depth – how many data points you use to collect information about each person you track. The potential of the database for ‘hybrid warfare’ depends on both factors: how many they know and how much they know about each of them.
An operation of this type may not be immediately successful in filling all the columns of information next to each name. But it details the data ambition the company wants to achieve over time. The chances of finding gold (actionable intelligence) multiply as the data set grows. And the chances that even a fraction of the key information database abroad (which is already 5 billion pieces of information and counting) will produce what is called “usable data” is enough motivation to stay invested in the market. draft.
Businesses are subject to regulations and elected legislatures can hold them accountable or ask them questions. In contrast, a Chinese company, from an opaque authoritarian configuration, that extracts big data in a more open democratic system does not have similar checks and balances.
Furthermore, propaganda – disinformation, disinformation, and fake news – has always been a high item on the agenda when countries go to war. But what big data now enables is to personalize the data for millions instantly, making quick response possible.
The sweep of Zhenhua’s targets, from politicians and CMs in the Center and the states to lawmakers in J&K and the Northeast, scientists at critical tech institutions to a variety of tech startups, and more than 6,000 defendants in a variety of crimes , all monitored for years. , produces a staggering volume of information that can be analyzed by sophisticated big data tools and processed according to the end user.
So the third question is:
Basically not much can be done … what’s the point then?
It’s not that you can’t do anything. Experts suggest that the government should educate citizens on cyber hygiene; a stricter level of hygiene for those in security-important positions. Since the mobile phone is becoming a data device and stores almost all personal information, “key people” should be careful when sharing personal information on social media or allowing platforms to track your geographic location, etc.
Perhaps not much can be done to stop data collection altogether, given what the technology allows and, in particular, given that open source public data is by definition open and public. Big platforms like Facebook and Twitter discourage automated scraping and bots, but recent events suggest this is more to maintain their monopoly on advertising data.
Yes, individual governments can force them to make mass scraping difficult, but overdoing it can change the nature of platforms and these companies are no easy prey. Therefore, without much concern about the source of the data and how it is collected, governments can invest in predicting potential strategic end uses for which foreign agencies can use the database. That means developing the ability to anticipate disinformation and propaganda campaigns. Given the bewildering pace of change in cybersecurity, new battle lines are being drawn.
📣 The Indian Express is now on Telegram. Click here to join our channel (@indianexpress) and keep up to date with the latest headlines
For the latest news explained, download the Indian Express app.
.