[ad_1]
ZecOps
A critical bug that has haunted iPhones and iPads for eight years appears to be under active attack by sophisticated hackers to hack high-profile target devices, a security company reported Wednesday.
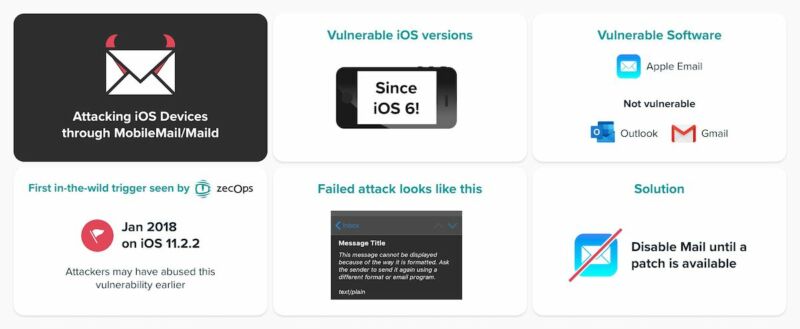
The exploit is triggered by sending emails with booby traps that, in some cases, do not require any interaction, and in other cases, only require a user to open the message, ZecOps researchers he said in a post. Malicious emails allow attackers to execute code in the context of default email applications, allowing messages to be read, modified, or deleted. The researchers suspect that the attackers are combining zero-day with a separate exploit that provides full control over the device. The vulnerability dates back to iOS 6 released in 2012. Attackers have been exploiting the bug since 2018 and possibly earlier.
Huge range
“With very limited data we were able to see that at least six organizations were affected by this vulnerability, and the full scope of abuse of this vulnerability is enormous,” wrote the ZecOps researchers. “We are confident that a patch for such issues with public triggers should be provided as soon as possible.”
The goals of the six organizations include:
- Individuals from a Fortune 500 organization in North America
- An executive of a carrier in Japan
- A VIP from Germany
- Managed security service providers in Saudi Arabia and Israel
- A journalist in europe
- Suspect: an executive of a Swiss company
Zerodays, or vulnerabilities known to attackers but not by the manufacturer or the general public, are rarely exploited in the wild against iPhones and iPads users. Some of the only known incidents were a 2016 attack that installed spyware on the phone of a dissident in the United Arab Emirates, a WhatsApp exploit in May last year that was broadcast with a simple phone call, and attacks that Google revealed on last august.
Apple has currently fixed the bug in the beta version for iOS 13.4.5. At the time of this publication, a solution had not yet been published in the general version.
The malicious emails that trigger the failure work by consuming device memory and then exploiting a heap overflow, which is a type of buffer overflow that exploits a memory allocation failure reserved for dynamic operations. By filling the heap with junk data, the exploit can inject malicious code that is then executed. The code triggers strings that include 4141 … 41, which exploit developers commonly use. The researchers believe that the exploit removes the email.
A protection known as randomization of the address space design prevents attackers from knowing the memory location of this code and therefore from executing in a way that takes control of the device. As a result, the device or app simply crashes. To overcome this security measure, attackers must exploit a separate error that reveals the hidden location of memory.
Little or no sign of attack
Malicious emails need not be prohibitively large. Normal-size emails can consume enough RAM using rich text, multi-part content, or other methods. In addition to a temporary device slowdown, targets running iOS 13 are unlikely to notice any signs that they’re under attack. In the event that the exploit fails on an iOS 12 device, the device will display a message saying “This message has no content.”
ZecOps said the attacks are closely targeted, but they only provided limited clues about the hackers who carried them out or the targets on the receiving end.
“We believe these attacks correlate with at least one nation-state or nation-state threat operator that purchased the exploit from an outside investigator in a Proof of Concept (POC) degree and used ‘as is’ or with modifications. minors (hence the 4141..41 strings), “wrote ZecOps researchers.” While ZecOps refrains from attributing these attacks to a specific threat actor, we are aware that at least one organization of “hackers” is selling exploits using vulnerabilities that exploit email addresses as the primary identifier. “
The most visible third-party organization selling advanced smartphone exploits is the Israel-based NSO Group, whose iOS and Android exploits over the past year have been used against activists, Facebook users, and undisclosed targets. NSO Group has come under fire for selling its products in countries with poor human rights records. In recent months, the company has promised to serve only organizations with better backgrounds.
It is generally contrary to the rules of the security community to disclose vulnerabilities without giving manufacturers time to release security patches. ZecOps said it launched its investigation ahead of a general launch solution because zero-day alone is not enough to infect phones, the bugs had already been mentioned in the beta, and the urgency created by the six organizations the company believes is are under active attack
To avoid attacks until Apple releases a general availability patch, users can install beta version 13.4.5 or use an alternative email application like Gmail or Outlook. Apple representatives did not respond to an email seeking comment for this post.