[ad_1]
Tool zoom he adapts to huge global demand and sudden success during the almost global social isolation caused by Covid-19. Thanks to this, ESET in Latin America provides key points that allow the user to configure it and thus increase the privacy and security of their video calls.
“The sudden success took Zoom by surprise: the company had a business model and privacy policy to support a free service, and suddenly they became the default tool for millions of organizations that have discovered the need to use. video conferencing, ”he said Camilo Gutierrez, Head of ESET Research Laboratory in Latin America.
“They had numerous privacy and security concerns, and they need time to adapt. This can be seen in the latest updates issued by the company to solve problems, and recent changes to its privacy policy, ”he added.
Tips to Avoid Security Concerns:
“Always use automatic generation, so each meeting will have its own“ Meeting ID. ” If the meeting ID is compromised, it will be used only for one meeting, and not for all that you organize.
This does not mean that a password is required to join the meeting. The password requirement must remain verified. However, to be effective, the ability to embed a password must be disabled.
– Starting a meeting with the camera turned off can help avoid an awkward moment. In this sense, users will be better off turning on the camera during a meeting if they want to or want to.

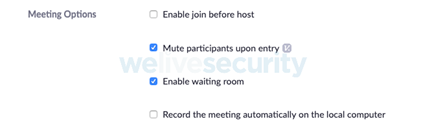
– Allow each participant to the conference room. Thus, complete control over visitors is in the hands of the owner.
In addition, you should consider the additional options available in the web client, and not in the application. After logging into the system in the “Settings” section in the “Personal” section of ESET, it is recommended to change the default settings for the following option:
– Delete the parameter with one click and prevent the password from being inserted into the meeting link. This means that each participant must enter a password to join the meeting. It is also important to set the following configuration points when creating a collection:
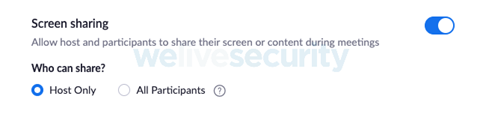
– Share the screen. The organizer can transfer the management of the meeting to another participant and make it possible. This recommendation may not be ideal for all scenarios. For example, those who use an educational tool may not want to transfer host control to a student. Therefore, it is important to consider the consequences of giving all participants access to the screen or, if it is better to limit this option only to the host.
– Disable background viewto prevent inadvertent display of sensitive content in public places, such as cafeterias.
– activate the “waiting room”, so users must go through the record filter before accessing the meeting.
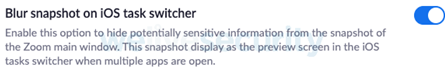
– Prevent display of sensitive data on task switcherspecifically for Apple iOS devices that take screenshots of open applications.
“The above recommendations do not replace the reader’s need to review Zoom’s privacy policy to ensure that it meets their requirements. Individuals and organizations must make their own decisions about which platform best suits their needs. From ESET, we always rely on education and awareness as the first security barrier to the safe use of the Internet, ”concludes Gutierrez.
In the context of the isolation of Covid-19, ESET shares #MejorQuedateEnTuCasa, A campaign that protects devices and content that help you make the most of your home and keep your little ones safe while they have fun online.
It includes: 90 free days of ESET INTERNET SECURITY to protect all home devices, a remote manual with recommendations for working from home without risk, ESET Academy, to access online courses that help take advantage of technology and Digipadres to read Tips on how to accompany and protect children online.
[ad_2]